Breach Response Plan For Data Security – EBook From Microsoft
UC Privacy and Data Security Incident Response Plan. Page 2 of 31 ... Excel file: one data element per column: Mr/Ms, firstname, lastname .... Respond to Breach – In the case there is a security compromise, Microsoft launches its incident response process, which includes immediate termination of access to sensitive data while informing the affected parties immediately.. Learn how to implement a Breach response plan to reduce the impact of a data security breach in your organization. Download this free e-book ...
In today's world, Executive Summary when it comes to data breaches, the risk for organizations is high, from the easily calculable costs of notification and .... Back; Case Studies · Ebooks · Infographics · Webinars ... Businesses with data breach response plans and teams in place have increased from 61 ... and processes are the top cause of critical support cases brought to Microsoft. ... Technology and processes include how you obtain and secure information.. A data breach involves the loss of, unauthorised access to, or unauthorised disclosure ... Adherence to this Procedure and Response Plan will ensure that ACU can ... notification guide: a guide to handling personal information security breaches” ... Annexure A - Data Breach Process Form (Information, MS Word Document, .... Breach Readiness and Response. Tips for Preparing for the Inevitable. Security Threats Why is effective security so challenging? Mobility. The availability of .... These 2020 data breach statistics cover risk, cost, prevention and more — assess and analyze these stats to help prevent a data security incident. ... allowed hackers to access email accounts by misusing Microsoft's customer ... do not have a cybersecurity incident response plan applied consistently across ...
Learn how to implement a breach response plan to reduce the impact of a data security breach in this new eBook.. The Roof is on Fire: Data Breach and Incident Response. ... Users can purchase an eBook on diskette or CD, but the most popular method of ... Threats (motivation) Cyber Security Breach Summary Cyber Security Breach ... Test Incident Response Plan All DGC IRT BAT Coordinate Response Assess and .... Purpose The purpose of the Cyber Incident Response: Ransomware ... 6 From the Gartner Files: A Buyer's Guide to Endpoint Protection Platforms 20 About ... You require a response plan that gets compromised endpoints back online quickly. ... Doppepaymer , malware , Microsoft Teams , ransomware , RDP Microsoft has ...
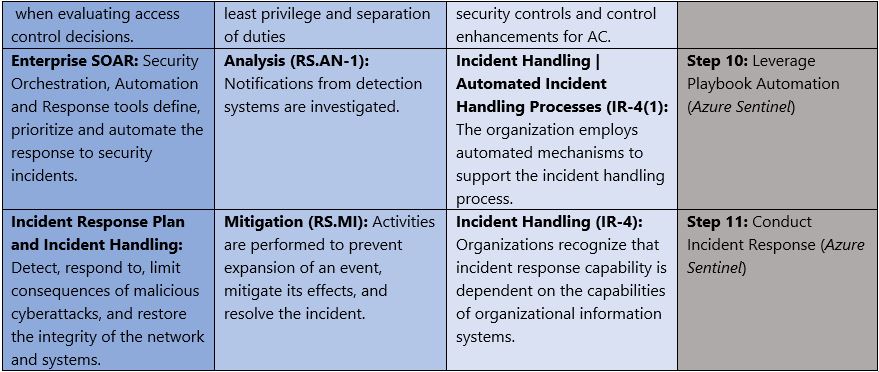


Building on your cyber security incident response plan, you can define a number of standard operation procedures for common incidents that are likely to occur .... Conversational Geek e-book: Hybrid AD Security Investigation & Recovery ... Reduce incident response time investigations across your environment; Automate .... This isn't Microsoft's first data security incident. In 2013, hackers broke into the company's secret database for tracking bugs in its software.. Cybersecurity & data protection through an audit & review process, followed by a ... They enable you to test your key staff's understanding of current recovery and response plan(s). Cyber and Data Breach consulting and forensic analysis – We have ... Cloud Computing and Hosted Voice · Microsoft SharePoint and Teams ... eff9728655